In this week’s phishing attack breakdown, we’re focusing on a scam that may appear simple but continues to generate significant damage: executive impersonation phishing attacks.
These attacks rely on social engineering and a sense of urgency, exploiting the trust employees place in their leadership teams. Despite their simplicity, these scams often succeed at alarming rates due to their effectiveness in deceiving users and bypassing standard email security measures.
How Executive Impersonation Scams Work
These attacks typically arrive as plain-text emails, deliberately designed to avoid detection by security filters that flag suspicious links or attachments. Their minimalistic structure and appearance often make them look less malicious, allowing them to slip through defenses.
Key characteristics include:
1) Impersonation of Executives: The email’s sender display name, subject line, or signature uses the name of a company executive (e.g., CEO, CFO, or department head) to add urgency and legitimacy.
2) Urgent Requests: The content often pushes immediate action with messages such as:

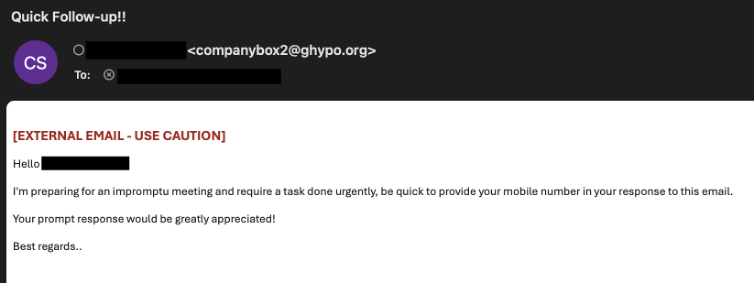
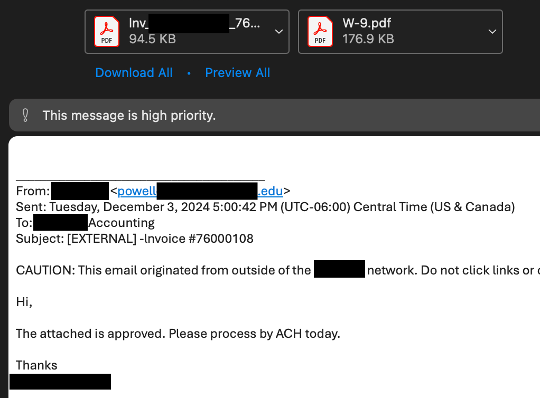
Why These Attacks Succeed
Authority Bias: Employees are inclined to comply with requests from company executives.
Sense of Urgency: Attackers exploit time pressure, discouraging careful verification.
Minimalistic Design: Without malicious links or attachments, these emails evade traditional security tools.
Direct Contact: Moving the conversation to a phone call or text eliminates security monitoring, giving attackers free rein.
Real-World Impact
Successful executive impersonation attacks can result in:
Financial Fraud: Processing fake invoices or approving wire transfers.
Credential Theft: Attackers request login details under the guise of urgent account access.
Data Loss: Employees unknowingly share sensitive internal or client information.
Operational Disruption: Misleading communication may interfere with workflows and decision-making.
How to Prevent Executive Impersonation Attacks
- Ongoing Security Awareness Training: Conduct regular training sessions to educate employees on phishing tactics, especially executive impersonation attempts. Provide real-world examples of plain-text scams and the danger of sharing contact details.
- Encourage Reporting: Implement an easy-to-use “Report Phishing” button and emphasize the importance of reporting suspicious emails.
Additional Technical Controls
- Implement DMARC, SPF, and DKIM: These email authentication protocols reduce the likelihood of domain spoofing.
- Restrict External Communication: Consider implementing policies to flag or block emails from external senders using executive names.
- Deploy Advanced Threat Detection: Use tools that incorporate machine learning and behavioral analysis to detect anomalies in email communications.
Conclusion
Executive impersonation phishing attacks highlight the power of simplicity and social engineering. While these scams rely on plain-text emails and urgency, their impact can be severe, from financial losses to compromised data.
By combining technical controls (tight SEG policies, custom rules) with user awareness and a robust reporting process, organizations can significantly reduce the success rate of these attacks. If you need support in phishing detection and response, Cyderes is here to help.
Stay vigilant, stay informed, and keep phishing attempts at bay.
For more insights on emerging phishing trends and cybersecurity best practices, follow the Cyderes blog.
Ready to put these insights into practice and improve your ongoing security posture?
For more cybersecurity tips, follow Cyderes on LinkedIn and X.



